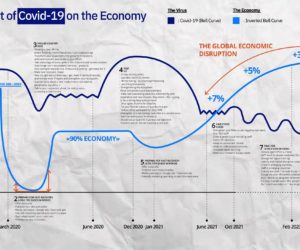
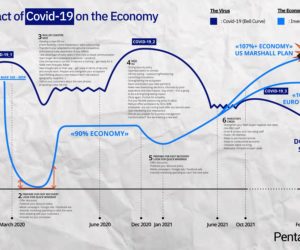
It’s natural that the first concern of many companies during te COVID-19 crisis has been to protect employees and assets in order to ensure business continuity. The challenge we see is to respond quickly while also addressing risk and security management plan. Below we share some insights from Pentalog’s response to the pandemic.
Stay Alert and React Fast
At Pentalog, we began tracking the epidemic spread and anticipating its consequences by December of 2019, realizing that it would only be a matter of time before the crisis will hit us. We prepared different scenarios and recommended to our clients to do the same.

We took preventive measures very early to reduce the spread of the Coronavirus infections.
Pentalog is a digital platform and most of our partners and collaborators operate online businesses. As such, we knew that we could maintain operational continuity as long as we kept our people safe and our IT infrastructure and security tools optimized at usual levels.
Our risk and security management plan consisted on three alert levels:
Level 1: Watch – Practice Usual Precautions
Level 2: Alert – Practice Enhanced Precautions
Level 3: Warning – Impose Drastic Measures
When Pentalog declared the alert level two, we also encouraged our employees to telecommute without closing the sites. For all colleagues who were returning from business trips, we imposed a mandatory 14-day self-isolation period.
Pentalog’s Work from Home Deployment Plan
On March 16, 2020, all 1,100 employees, on three continents, started working from home for an indeterminate period. Their safety is our main priority. A staggered shift to work from home mode allowed us to assess and consolidate the IT infrastructure in order to handle traffic spikes we had never seen before.
Pentalog spent two months preparing a work from home deployment plan. Prior to enacting the decision, we took several additional measures:
- Split the charge in two different VPN gateways to guarantee the availability and performance of infrastructure.
- Increased the internet speed so all our colleagues benefit of excellent internet connection.
- Strengthened patch management processes.
- Increased security monitoring (antispam, antivirus tools and security events management tool) to detect suspicious behavior or unauthorized system changes on the network.
- Prepared a stock of spare equipment for VPN and inventory management.
- Updated the company’s security policies and guidelines.
- Prepared questionnaires for all users in order to detect connectivity issues.
- Closely monitored each location to make informed decisions on a site-by-site basis.
While Pentalog team members already had the possibility of telecommuting before the outbreak, we streamlined our internal process and equipped people with the tools they needed to ensure productivity, while making sure our communication on security awareness continues.
Once we provided remote work options for employees at all Pentalog locations, the number of VPN connections per day has increased more than 10 times, on average.
So, the main challenge for the upcoming period is to maintain infrastructure stability and security protection while our development teams ensure the highest levels of productivity.
Create Business Continuity Procedures
As far as possible, companies should take advantage of the current moment to formalize a business continuity plan related to key people and processes. Being able to handle any incident effectively can have a positive effect on the company’s reputation and market value, and it can increase customer confidence.

Experts say now is the time to usher in systemic economic change.
The COVID-19 crisis shows us that it is possible to make remarkable transformational changes practically overnight. A key aspect to this digital transformation is to analyze customers’ needs and trends in the face of potential disruptions.
To optimize infrastructure and operations, here’s what companies should pay attention to:
- Update the job rotation policy to ensure that the company will still function if key employees get sick.
- Have back-up plans, incident response strategies.
- Foster work community and encourage strong communication between team members.
- Review mobile device management policy to ensure that company owned mobile devices has MDM software installed.
- Review the policy for allowed software on company’s assets.
Alert on Cyber Security Risk
We have all seen that “Coronavirus” phishing attacks are increasing in this period, so stay alert. Sophisticated attackers are everywhere, and we always need to be ready to rapidly respond not just in a potential crisis. Defending against online threats should be a continuous process that evolves and matures as the threat landscape changes.
Maintain proper cybersecurity hygiene to help prevent common (but still harmful) threat tactics such as phishing, DDoS attacks, credential theft, and malware injection.
- Ensure that company assets have adequate security protection: up-to-date software, antivirus, firewall etc.
- Give employees points of contact in case of security incidents.
- Enforce strong password policies.
- Always work over secure channels: https, fttps, secure VPN, etc.
- Don’t click suspicious links you receive through email and don’t open documents so easily: .exe (especially dangerous), .zip. .rar (archive often have something to hide and can bypass weak antivirus solutions).
- When you have suspicions, always report them. Find out who is responsible and speak out your suspicion.
- Provide policies for Acceptable Use Policy on company assets.
- Ensure your home wi-fi is secure: use strong encryption protocols (WPA2, WPA3), use strong wi-fi password (absolutely no default passwords) and, why not, hide your SSID. If your home router offers the ability to control who connects to your network, adopt a whitelisting policy and only allow devices you trust.
- Avoid connecting to public/unknown wi-fi.
- Ensure firewall is working.
- It’s a good idea to keep the habit of blocking your PC while not in front of it.
- Continue your training on security, as everybody has to be even more attentive and take care to any strange online communication.